CYBERSECURITY
The human Touch
Preventing human error in cybersecurity is an ongoing challenge for processors
You have an extensive cybersecurity infrastructure in place, with the latest and greatest technology, all up-to-date on patches and updates and a highly trained, motivated staff of experts to help protect your data.
Then an employee clicks on a link in a phishing email. Or connects a personal smartphone to the WiFi to show coworkers the latest TikTok sensation. Or writes down a password on a Post-It note because they’re tired of having to remember it.
Much like almost any aspect of an operation, cybersecurity comes down to one simple tenet: It’s only as good as the people who are tasked with making it work on a day-to-day basis. And if those people are finding workarounds or ignoring policies, the best-laid cybersecurity plans suddenly fall apart.
But if they’re properly trained, understand their importance to cybersecurity efforts and are engaged in making cybersecurity successful, then they can be your greatest asset, says cybersecurity consultant Craig Reeds.
“Employees are the last line of defense when it comes to cybersecurity,” says Reeds. “Many cybersecurity professionals refer to employees as the weakest link or the largest attack vector; these statements send the wrong message. I prefer to say that employees are the last line of defense when it comes to cybersecurity. A well trained, informed employee can stop a great number of attacks, without even realizing it.”
Keeping employees engaged and motivated to be that last line of defense is the challenge. But it is possible to do. It requires a solid training plan, understanding the likely lines of attack and making sure that employees can do their job with cybersecurity as an aspect of it, not a hindrance.
Casey Laughman, Editor-in-Chief

Part of cybersecurity is ensuring that unauthorized personnel can’t access networked equipment. So when someone shows up with a load of boxes, make sure they’re supposed to be there and only go where they’re allowed to go. Photos courtesy of Getty Images/ FilippoBacci
Training, not overtraining
Most organizations have a cybersecurity training program, either as part of new hire training, job-specific training or ongoing training. But just having a training program isn’t enough, says John Livingston, CEO, Verve Industrial.
“We believe that ‘training’ is relied upon too much,” says Livingston. “While these programs are helpful, the key is the regular updating of training with programs such as email phishing campaigns. Critical to these regular programs is that they are more than ‘gotchas’ and that follow-up and training is done for those that do fall victim to these simulated attacks.”
As Livingston says, training is one thing; effective training is another thing entirely. If cybersecurity training is going over the same old thing and not actually engaging employees, it’s not going to be effective.
Consider the most common employee error in cybersecurity, which is employees clicking on links in phishing emails. Training needs to teach employees how to recognize potential phishing attempts and whom to contact in IT to determine if an email is safe, but it also needs to train IT employees to communicate phishing attempts to the entire organization as soon as possible.
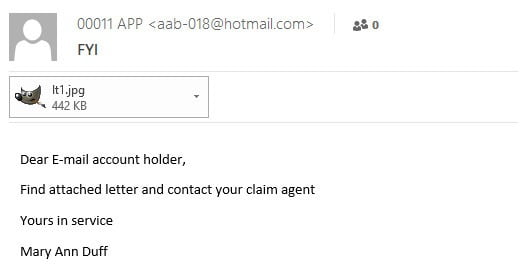
Most phishing emails are pretty easy to identify, such as this one. But more sophisticated efforts that appear to be from someone within the organization can fool employees into clicking links they shouldn't. Photo illustration by Casey Laughman/Food Engineering
“Currently, the biggest threat to operational technology networks is ransomware, which can find its way onto networks in a variety of ways, but the infamous phishing email is still the most widely reported attack vector,” says Chuck Tommey, IT/OT networking consultant, Siemens Industry. “Luckily, the best defense does not need to be very expensive but does take a considerable amount of time and effort, and that is a well-trained workforce. The training should include topics like the overall importance of cybersecurity to the company, social engineering, and phishing, how to recognize a possible cybersecurity incident, and what to do and what not to do when an incident is suspected.”
Training should not stop after the initial session. That doesn’t mean that employees need to constantly attend training sessions; in many cases, an email from IT or senior management explaining new threats and how to deal with them is sufficient. But refreshers are important. Reeds recommends a combination of reminder emails, posters in high-traffic areas with key points, and some sort of training with a quiz to ensure employee engagement several times a year.
Training can also be tailored to specific roles, says Tommey. For example, employees that only have access to typical office applications can receive annual training with quarterly phishing and/or social engineering testing. As access for an employee increases, so should training to ensure they understand and implement best practices to protect data.
“Additional training may be required if an employee fails a specific number of tests or if large numbers of employees fail one type of test,” says Tommey. “The training should also be more intense and regular for those with defined responsibilities for cyber incident response and disaster recovery. For these roles, table top incident response exercises and practice disaster recovery scenarios are considered highly effective and necessary to determine readiness. These training sessions can generate invaluable feedback to improve a cybersecurity program’s policies and procedures.”
"Employees are the last line of defense when it comes to cybersecurity." — Craig Reeds, cybersecurity consultant
Identifying lines of attack
The most common cybersecurity threat facing most companies these days is phishing attacks, where an employee clicks on a link in an email and triggers a cybersecurity breakdown. But they’re not the only kind of attack processors need to watch out for.
Social engineering has changed drastically from the days of hackers calling up an employee and talking their way into a network. But it still exists, and the concept is basically the same: An outsider uses some sort of distraction technique to gain access to a network or an area where they shouldn’t be. The reason why it’s so damaging is simple: Having the access of internal personnel allows for the greatest potential to wreak havoc.
“There have been cases in food and beverage as well as other industries where significant control system cyber impacts were caused by internal personnel,” says Joe Weiss, managing partner, Applied Control Solutions LLC. “In some cases, the actions of the internal personnel were implausible. However, in almost all these cases, because the actions were initiated by internal personnel, the incidents were viewed as unintentional. The impacts can be the same whether the actions were malicious or unintentional.”
These kinds of attacks come from a number of different angles; everything from connection requests on LinkedIn that pump employees for information on what they do and who they work for to someone approaching a door with their hands full to play on the natural instinct to help them out by opening the door for them. If they’re allowed to roam freely because they “look like they belong” because they’re making a delivery or something like that, then suddenly passwords written on Post-It notes become a very big problem.
To combat this, employees should be taught to understand what is and isn’t appropriate information to share, and how to respond if they see a red flag in a request for information or help from anyone, much less an outsider.
“Using real insiders asking for inappropriate information is probably the best training,” says Tommey. “If an employee recognizes the inappropriate request and learns to say no to a known leader in the company, then resisting the odd request from an unknown person will become much easier. Don’t forget to or avoid training and testing the folks at the top. Ownership or C-level executives have access to some of the most important information in the company.”
"If an employee recognizes the inappropriate request and learns to say no to a known leader in the company, then resisting the odd request from an unknown person will become much easier."
— Chuck Tommey, IT/OT networking consultant, Siemens Industry
